 |
VPN
Virtual Private Networks (VPNs) are one of the latest buzzwords
around the computer networking industry. VPNs connect users across a
shared, public network providing connectivity to centralized
applications and resources. The goal of the Virtual Private Network is
to take a low cost public network like the Internet and, using complex
security measures, create a "private network". With the
number of remote access users increasing significantly, companies are
seeking solutions to meet this need. VPNs or "extranets" meet
this unique need with improved access and reduced costs.
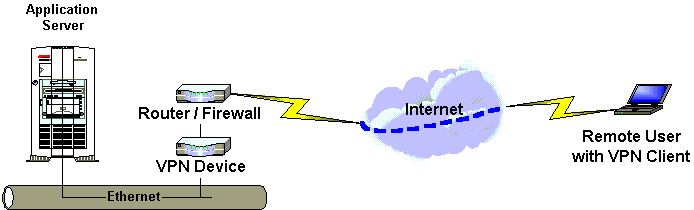
A Virtual Private Network, in a very simplified manner, is
illustrated in the diagram above. The corporate network is connected to
the Internet with firewall services implemented. Remote users with VPN
Client Software connect to the Internet via a local ISP (Internet
Service Provider) like, America Online, Rogers or BellSouth.Net. The
connection is secured in the VPN Tunnel through the Internet public
network.
VPNs offer many benefits to corporate networks including:
-
Cost savings for dedicated and dial-up connections
-
Extended networking with large geographical coverage
-
Access to local service provider networking expertise
-
Simplified enterprise networking and WAN operations
-
Increased networking reliability with improved uptime
Virtual Private Networks offer the rapid enabling of new services
and facility connections across the globe. VPNs are still an end-to-end
network exhibiting most of the same characteristics of a private WAN
infrastructure. In designing and implementing a VPN, organizations
should keep the following issues in mind to insure success:
-
Designs should be scalable to address the needs of increased
business requirements
-
Must assure end-to-end reliability
-
Provide for the integration of legacy protocols and services
-
Allocate bandwidth to ensure critical applications receive
appropriate throughput
-
Maintain security of corporate data
Of course as with most networking implementations, companies may
outsource key aspects of the VPN infrastructure to a service provider
or they may handle these responsibilities internally. As the network is
extended with VPN technology, a strict set of business requirements
must be met for a successful implementation. These requirements
include:
-
Minimized Risk---moving from a dedicated infrastructure to a
shared infrastructure, possibly utilizing the Internet, presents new
security and auditing challenges. The network must be extended or
"opened" to remote users, suppliers and partners while
assuring the confidentiality and integrity of the data.
-
Scalability---the rapid addition of mobile users, geographically
dispersed sites, and new business partners requires the ability to
grow the network, upgrade hardware, software, bandwidth, and
services with speed and accuracy.
-
Reduced total cost of ownership---to realize the savings of a
shared infrastructure, the implementation of new technologies and
support of additional network users must be handled without
increasing the operations staff and budget. This is a significant
issue due to the complexities of the VPN technology and if not
handled correctly this could easily erase the cost savings provided
by the new technology.
-
Reliability---the move to a shared infrastructure presents new
challenges in delivering and monitoring the reliability of the
network service provided.
Zebase combines Rogers and Sympatico communication offerings with our Design and
Implementation Services to provide a complete VPN solution. Zebase completes the solution with leading products from Cisco Systems,
Microsoft. Contact Zebase to discuss your specific
requirements and to begin leveraging the power of VPNs today.
VPNs give you an easy-to-implement, easy-to-manage
solution to the problem
of how you allow these remote users access.
Conventional dial-up access still works fine, but
it can be expensive to implement, painful to manage,
and vulnerable to attack.
VPNs offer a way around these problems by offering low
initial and ongoing
cost, easy management, and excellent security. Windows
2000’s Routing and
Remote Access Service (RRAS) component includes two
complete VPN implementations:
|
 |







